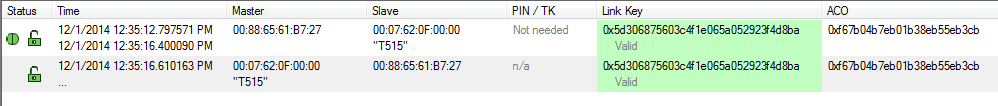
Security Pane
The Security pane is where the Frontline software identifies devices with captured traffic (![]() ) that contain pairing, authentication, or encrypted data. The pane will show fields for entering keys, and will show if the keys are valid or invalid.
) that contain pairing, authentication, or encrypted data. The pane will show fields for entering keys, and will show if the keys are valid or invalid.
Successful decryption of captured data requires datasource receipt of all the critical packets and either :
- be given the link key by the user, or
- observe the pairing process and determine the link key.
See Sodera: Critical Packets and Information for Decryption for a description of the critical packets. The Security pane will identify the type of key required for decryption.
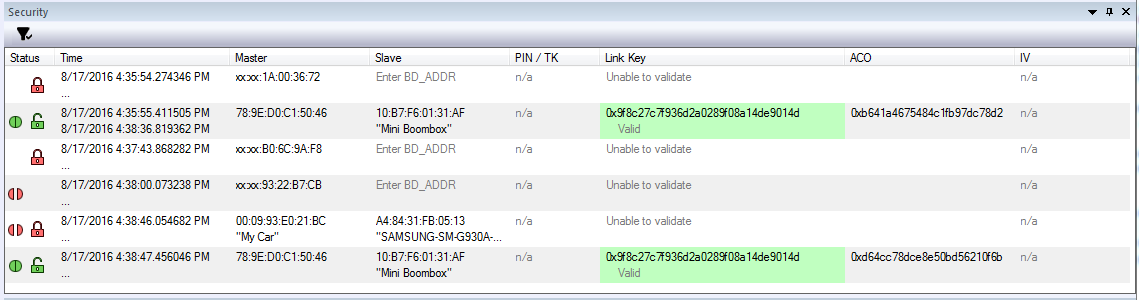
Sodera Datasource Security Pane
The Security pane shows events in the current capture. When the Record button is clicked, all devices with active traffic that require decryption are shown. Security events appear in starting time order with the most recent event at the bottom.
-
Status: displays icons showing the pairing and encryption/decryption status.
Icon Description 
Pairing/Authentication attempt observed but was unsuccessful 
Devices successfully Paired/Authenticated. 
Encrypted: traffic is encrypted but there is insufficient information to decrypt. See Sodera: Critical Packets and Information for Decryption for a description of the critical packets. 
Decrypted - Time: Beginning and end time of the security context. No end time is indicated by an "…". Beginning time is shown in the first row of the grouping. End time is shown in the second row.
- Master: The BD_ADDR of the master device in the link. If the friendly name is available it will show on the second line.
-
Slave: The BD_ADDR of the slave device in the link. If the friendly name is available it will show on the second line.
Note: If the Master and Slave switch roles another entry will appear in the Security pane
Role Switch Example
- PIN/TK:
- Classic Bluetooth® :
- Legacy Pairing PIN: 1 to 16 alphanumeric character PIN
- Bluetooth low energy
- PIN: 6 digit numeric passkey (000000 - 999999)
- Out-of-Band Temporary Key (OOB TK): 32 digit hexadecimal number
- Classic Bluetooth® :
- Link Key
- Classic Bluetooth® , 32 digit hexadecimal number
- Bluetooth low energy, 32 digit hexadecimal number
- The Link Key cell displays "Enter link key" in gray when the link key is unknown. When a link is invalid the cell has a light red background and indented gray text under the link key says "Invalid". When a link key is valid the cell has a light green background and indented gray text under the link key says "Valid" (if the link key was transformed from the entered link key the text is "Valid (Reordered)".
- If Sodera is Analyzing and a link key has not been entered, "Stop analyzing to enter link key" appears in the device Link Key cell. Click the Analyzing button to stop the analysis, and type or paste in the link key.
- Users can enter the device security information by typing directly on the device fields PIN/TK and Link Key. An invalid entry will display a red background and a warning Invalid.
- ACO: Authenticated Ciphering Offset is used by the devices for generation of the encryption key in Classic Bluetooth.
- IV: Initialization Vector is displayed for both Bluetooth low energy encryption and Classic Bluetooth Secure Connections/AES encryption.. The slave will use the IV in starting the encrypted communications.
Security Pane Toolbar
The Security pane toolbar appears at the top of the pane. The Security Pane Filtering tool is the only tool available. The default state of the tool is not enabled, showing available security information for all active devices in the Wireless Devices pane. When the tool is clicked, that is active, only the available Security Pane only shows the security context associated with the wireless devices that have been selected for analysis.
Should device selection change by selecting or deselecting devices, the Security Pane display will change with the device context.