Pairing
A Bluetooth low energy device that wants to share secure data with another device must first pair with that device. The Security Manager Protocol (SMP) carries out the pairing in three phases.
- The two connected Bluetooth low energy devices announce their input and output capabilities and from that information determine a suitable method for phase 2.
- The purpose of this phase is to generate the Short Term Key (STK) used in the third phase to secure key distribution. The devices agree on a Temporary Key (TK) that along with some random numbers creates the STK.
-
In this phase each device may distribute to the other device up to three keys:
- the Long Term Key (LTK) used for Link Layer encryption and authentication,
- the Connection Signature Resolving Key (CSRK) used for data signing at the ATT layer, and
- the Identity Resolving Key (IRK) used to generate a private address.
Of primary interest in this paper is the LTK. CSRK and IRK are covered briefly at the end.
Bluetooth low energy uses the same pairing process as Classic Bluetooth: Secure Simple Pairing (SSP). During SSP initially each device determines its capability for input and output (IO). The input can be None, Yes/No, or Keyboard with Keyboard having the ability to input a number. The output can be either None or Display with Display having the ability to display a 6-digit number. For each device in a paring link the IO capability determines their ability to create encryption shared secret keys.
The Pairing Request message is transmitted from the initiator containing the IO capabilities, authentication data availability, authentication requirements, key size requirements, and other data. A Pairing Response message is transmitted from the responder and contains much of the same information as the initiators Pairing Request message thus confirming that a pairing is successfully negotiated.
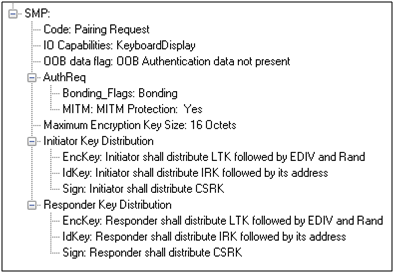
Sample Initiator Pairing Request Decode (ComProbe Frame Display, BPA 600 low energy capture)
In the sample SMP decode, in the figure at the right, note the “keys” identified. Creating a shared, secret key is an evolutionary process that involves several intermediary keys. The resulting keys include,
- IRK: 128-bit key used to generate and resolve random address.
- CSRK: 128-bit key used to sign data and verify signatures on the receiving device.
- LTK: 128-bit key used to generate the session key for an encrypted connection.
- Encrypted Diversifier (EDIV): 16-bit stored value used to identify the LTK. A new EDIV is generated each time a new LTK is distributed.
- Random Number (RAND): 64-bit stored value used to identify the LTK. A new RAND is generated each time a unique LTK is distributed.
Of particular importance to decrypting the encrypted data on a Bluetooth low energy link is LTK, EDIV, and RAND.
