BPA
There are four ways to sniff Bluetooth® wireless technology communications using the ComProbe BPA 600 Dual Mode Bluetooth Protocol Analyzer. You choose the mode you will be using by selecting one of the following radio buttons on the Devices Under Test tab in the BPA 600 datasource dialog:
By selecting the "LE Only" radio button under the "Devices Under Test" tab you can configure the BPA 600 protocol analyzer for sniffing Bluetooth low energy communications.
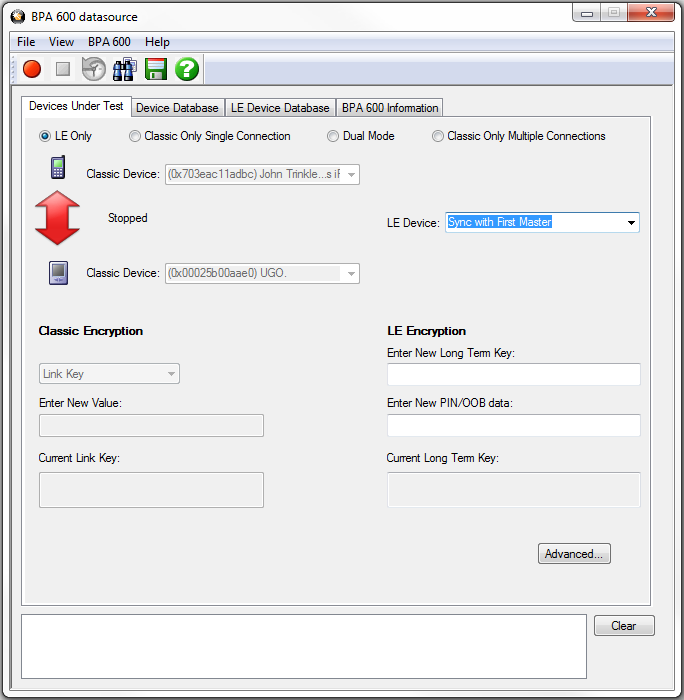
BPA 600 Devices Under Test - low energy
The default value in the LE Device drop down is Sync with First Master. To begin sniffing Bluetooth low energy simply click the red button to start. The analyzer will capture packets from the first Master that makes a connection . To capture the advertising traffic and the connection(s), you must specify a device address.
Specifying the LE Device Address and Encryption
-
If you would like you may specify the LE device you are testing by typing in or choosing its address (BD_ADDR). You can type it directly into the drop down, or choose it from the existing previous values list in the drop down.
To enter the device manually type the address - 12 digit hex number (6 octets). The "0x" is automatically typed in the drop down control.
Once you have the devices address identified, the next step is to identify the Encryption.
- Enter the Long
Term Key for the LE Encryption.
The Long Term Key is similar to the Link key in Classic. It is a persistent key that is stored in both devices and used to derive a fresh encryption key each time the devices go encrypted.
Note: If you use Copy/Paste to insert the Long Term Key , Frontline will auto correct (remove invalid white spaces) to correctly format the key.
- Enter a PIN or out-of-band (OOB) value for Pairing.
This optional information offers alternative pairing methods.
Click here to see how to capture data after completing the configuration.