Legacy Pairing (Bluetooth 2.0 and earlier)
In legacy pairing, this link key is derived from a shared PIN code, the master’s Bluetooth clock, the master’s BD_ADDR and a random number that is passed between the two devices. If the sniffer has all of this same data, it can create the link key in the same way that the devices do. The sequence of events used to create this key, or pairing process, is shown in the ComProbe software Frame Display below.
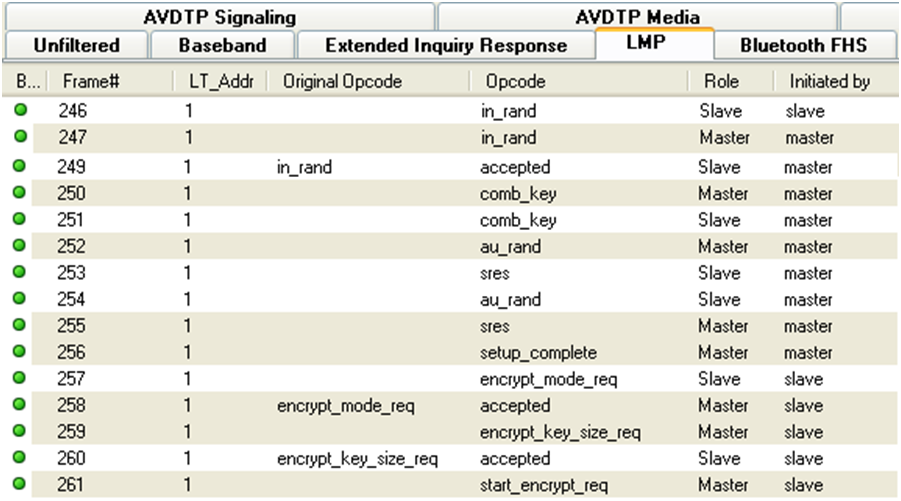
Frame Display
Frame 247 is the LMP_in_rand which is where a random number generated by the master is passed to the slave. The slave acknowledges that it has accepted the number in frame 249. The initialization key has been passed to the slave and is now shared by both devices. Both devices now independently generate combination keys.
In frames 250 and 251, the combination keys are passed between master and slave. In frame 252, the master sends its LMP_au_rand. This is the random number that has been encrypted using the link key that master has calculated. The slave then responds with frame 253, an LMP_sres confirming that it was able to compute the same number. That process is repeated in the other direction (slave to master) in frames 254 and 255. This completes the authentication between devices, and the setup_complete message is sent and the slave requests encryption mode in frame 257, and the master accepts in frame 258. The actual encryption starts after the start encryption request in frame 261.
In order for the ComProbe software to decrypt an encrypted Bluetooth conversation, the ComProbe software must compute the same link key being used by the devices being sniffed. Since this link key is never sent over the air, the ComProbe software must have all of the same information the devices being sniffed have so that it can calculate the same link key that each of the two devices does. To decrypt successfully, the ComProbe software must know the PIN code and capture:
- The LMP_in_rand
- Both LMP_comb_keys
- Both LMP_au_rand/LMP_sres pairs.
If any of these are missed, the ComProbe software will not be able to decrypt. If you capture encrypted data and find that everything captured after the LMP_start_encryption_request is in error, look back at the LMP frames previous to that and you’ll probably find one or more of these missing. The Start Encryption Request with also be marked by the ComProbe software with an error that indicates that the link key calculated by the ComProbe software is different from the one used by your devices.
